The add certificate tool supports importing certificates with the following formats and extensions:
-
If your PEM file has an extension of .pem, rename it to .cer or .crt before using the Add Certificate tool.
-
PKCS#7: .p7b
This tool has several purposes, including:
- It can be used to import certificates generated outside the enterprise PKI
 A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. environment—such as those purchased from a commercial certificate vendor or generated by a non-Microsoft or non-EJBCA CA
A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. environment—such as those purchased from a commercial certificate vendor or generated by a non-Microsoft or non-EJBCA CA A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA..
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA.. - It can be used to import certificates that would not be automatically imported during a synchronization of configured Microsoft or EJBCA CAs such as root CA certificates or certificates with unusual key types (e.g. Dilithium) that aren’t supported by synchronization.
- It can be used to import certificates acquired using CSRs generated by Keyfactor Command and issued by a CA not managed using Keyfactor Command to allow for ongoing management with Keyfactor Command.
- It can be used to push a certificate with the associated private key
 Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. out to a certificate store when you have the appropriate .pfx or .p12 file available.
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. out to a certificate store when you have the appropriate .pfx or .p12 file available.
-
It can be used as a quick shortcut to push a certificate without a private key out to a certificate store when you have the certificate file in hand and don’t want to search for the certificate in Keyfactor Command in order to push it out to the certificate store.
Before you can add a certificate to a certificate store with this option, you must first add the certificate store in Keyfactor Command (see Certificate Stores) and install, start, and approve the orchestrator
 Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. (see Orchestrator Management and the .
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. (see Orchestrator Management and the .
If you import a certificate that has either already been imported via a synchronization task or has been manually imported previously, the certificate will not be re-imported. You will receive a notification message, when you save it, if the certificate already exists in the Keyfactor Command database. Any metadata![]() Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. currently stored in the database for that certificate will be displayed in the metadata fields on the page (for .cer and .crt format certificates), and any changes you make to the metadata on this page will overwrite the existing metadata for the certificate when you complete the import (for all certificate formats).
Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. currently stored in the database for that certificate will be displayed in the metadata fields on the page (for .cer and .crt format certificates), and any changes you make to the metadata on this page will overwrite the existing metadata for the certificate when you complete the import (for all certificate formats).
To use the add certificate tool
- In the Management Portal, browse to Certificates > Add Certificate.
- In the Add Certificate section of the page, click the Upload button to open a browse window.
- In the browse window, browse to select the certificate you wish to import.
-
For a .pfx or .p12 file, when prompted enter the password for the file and Save. This will open the Add Certificate page, which will allow you to change/add metadata and choose certificate locations to deploy the certificate to. Set PFX Password allows you to reenter the password once you have uploaded the certificate.
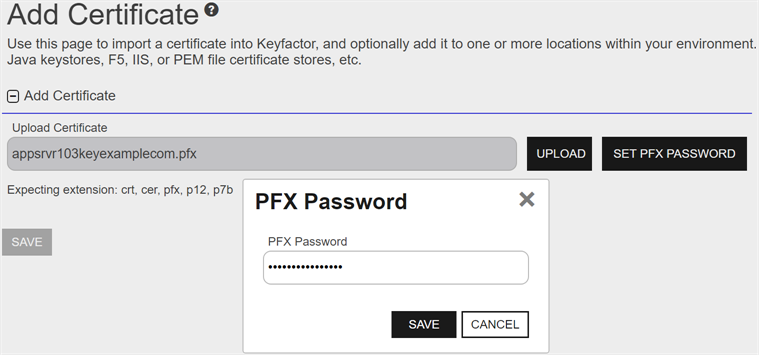
Figure 52: Add Certificate Password for PFX/p12
-
In the Certificate/PFX Details section of the page, review the certificate information.
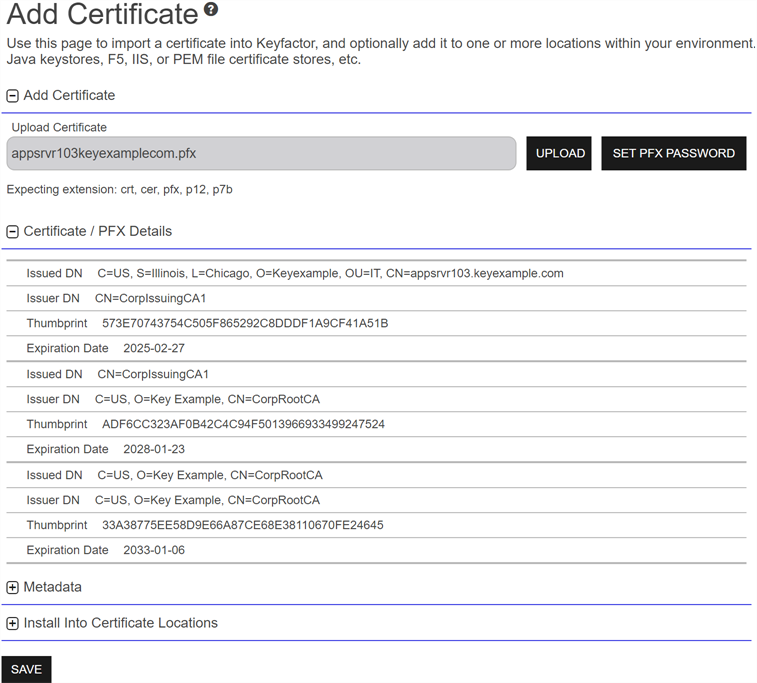
Figure 53: Add Certificate Information
-
In the Metadata section of the page, populate the metadata fields as appropriate for the certificate. Metadata fields that have been designated as required on a system-wide or template
 A certificate template defines the policies and rules that a CA uses when a request for a certificate is received.-level basis will be marked with *Required.
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received.-level basis will be marked with *Required.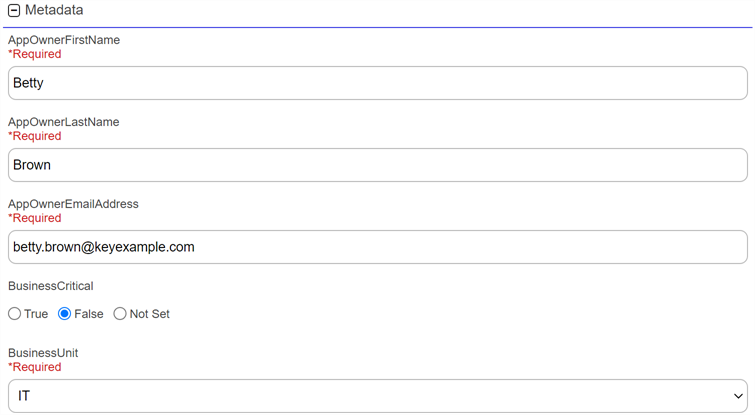
Figure 54: Add Certificate Metadata
-
In the Install into Certificate Locations section of the page, select each certificate store location to which you want to distribute the certificate, if desired. To do this, click the Include Certificate Stores button. This will cause the Select Certificate Store Locations dialog to appear. Make your certificate store selections in this dialog as described in Select Certificate Store Locations, below, and click Include and Close. You will then see some additional fields on the page. Populate these as per Add to Certificate Stores and Information Required for Certificate Stores, below.
 Select Certificate Store Locations
Select Certificate Store Locations
The Select Certificate Store Locations dialog allows you to run queries against your certificate store list to select which store(s) to deploy a selected certificate to. Check the box next to each certificate store location to which you want to distribute the certificate.
Note: Only compatible certificate stores and only stores in containers to which you have permissions are shown on the grid.Tip: You may change the search results by using the search fields at the top of the dialog. All of the Keyfactor Command grid search features are available to assist your search. See Using the Certificate Store Search Feature for more information on the available search fields. The default search criteria is AgentAvailable is equal to True.The actions on the Select Certificate Store Locations dialog are:
-
Include
Click this to add the selected certificate store(s) to your certificate selection and leave the search dialog open for further searches.
-
Include and Close
Click this to close the search dialog and add the selected certificate store(s) to your certificate selection, which will then be displayed and ready for updates as per the instructions in Add to Certificate Stores.
-
Close
Click this to cancel the operation and return to the main page with no certificate stores selected.
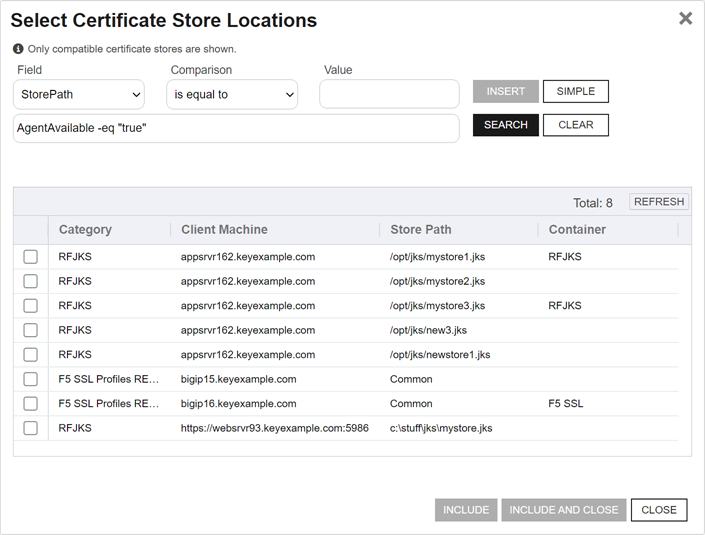
Figure 55: Select Certificate Store Locations Dialog
 Add to Certificate Stores
Add to Certificate Stores
The Add to Certificate Stores page appears once you select at least one certificate store to distribute your certificate to. It includes a grid section with a series of tabs that display a tab for each type of certificate store selected with a list of the selected stores under each tab. The header section of the dialog shows global options that apply to the add job as a whole:
-
Include Certificate Stores
You may return to the Select Certificate Store Locations dialog by clicking Include Certificate Stores above the grid. The current selections will be retained.
-
Schedule when to run the job for the certificate store
In the Schedule dropdown, select a time at which the job to add the certificate to the stores should run. The choices are Immediate or Exactly Once at a specified date and time. If you choose Exactly Once, enter the date and time for the job. A job scheduled for Immediate running will run within a few minutes of saving the operation. The default is Immediate.
Click Remove at the top of the grid to remove the selected certificate store from the page. The certificate will not be added to the store.
For each selected certificate store you can apply the following actions:
-
Overwrite
Check Overwrite below the grid to overwrite any existing certificate in the same location and with the same name or alias for the selected certificate store type.
-
Alias
Add an Alias below the grid, if applicable, for the certificate store type. See the Information Required by Certificate Store section, below, for more information.
Note: The tab heading of the certificate location will display an alert if an alias is required for the location. If Supports Custom Alias is set to Forbidden on the certificate store type, the Alias field will not display unless Overwrite is checked on this page.
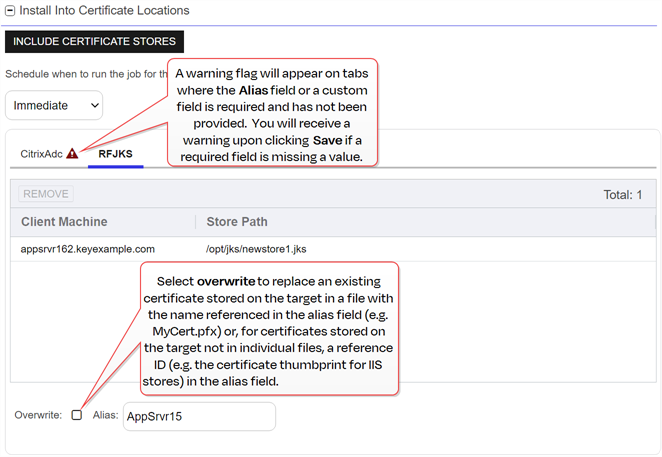
Figure 56: Add Certificate—Install into Certificate Locations

Figure 57: Alias Required Alert on Save
 Information Required by Certificate Stores
Information Required by Certificate Stores
Each type of certificate store has different requirements for providing an alias or other additional information.
The certificate store type fields that are relevant to certificate store use are:
-
Supports Entry Password
If your certificate store type has this enabled, you will have the option to enter a password for the certificate entry in the certificate store on the addition of an entry into the certificate store.
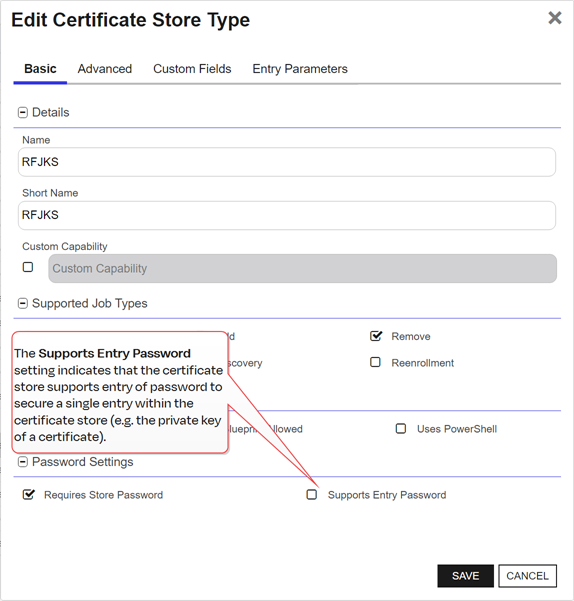
Figure 58: Certificate Store Type Configuration: Basic Tab
-
Supports Custom Alias
A value of Required indicates that a custom alias will be required when a certificate is added to a certificate store. Optional indicates an alias can be associated with the entry if desired. If your certificate store type sets this to Forbidden, the Alias field will not display when adding a certificate to a certificate store unless Overwrite is checked on the add page. In this case, you’re not associating an alias with the certificate you’re adding to the store but rather specifying the alias of the certificate already in the store that you wish to replace (in function) with the new certificate you’re adding.
The format of custom alias values varies depending on the certificate store type. In many cases, the alias is the thumbprint of the certificate. In some cases, it’s the file name of the certificate file or a custom alias provided at the time the certificate was added to the certificate store. For instance:
-
For an Amazon Web Services (AWS) store, the alias is the internal ID assigned by Amazon (the Amazon resource number or ARN). Provide the entire contents of the Alias/IP from this field when entering an alias for overwrite. For example:
arn:aws:acm:us-west-2:220531701668:certificate/88e5dcfb-a70b-4636-a8ab-e85e8ad88780 -
For F5 stores using the Keyfactor custom-built F5 Certificate Store Manager extension (see ), the alias is the file name used to store the file in the device file system, minus the extension (e.g. use alias MyFile for a file named MyFile.crt). Aliases should be entered without spaces. Note that certificate names are case sensitive.
Note: Keyfactor Command will automatically strip out any spaces between the octets in thumbprints in the alias field, so it does not matter whether you enter the thumbprint with or without spaces.Tip: When adding a certificate to a certificate store, you have the option to overwrite an existing certificate with the current certificate. If you choose this option, you will need to provide the alias of the certificate you wish to overwrite. Find the alias values by navigating to Management Portal > Certificates > Certificate Search. Select the certificate you wish to overwrite and double-click, or click Edit, from the grid header or right-click menu. Choose the Locations tab and double-click on the Location Type (this must have a number other than zero in the Count column) to open the details dialog. The Alias field holds the information that may be required for an overwrite.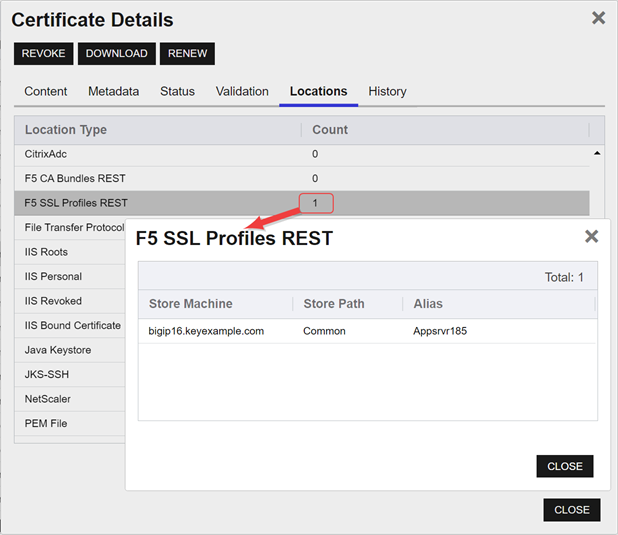
Figure 59: Example: Certificate Location Details for a JKS Location
-
-
Private Key Handling
When adding a certificate to a certificate store, if you select a certificate that does not have an associated private key, certificate stores with this option set to Required will not appear as available stores to which the certificate can be added. If this option is set to Forbidden and the selected certificate has a private key, the private key will be ignored and only the public key
 In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. will be delivered to the target.Note: Private keys are always available in PFX
In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. will be delivered to the target.Note: Private keys are always available in PFX A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. Enrollment
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. Enrollment Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA)..
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA)..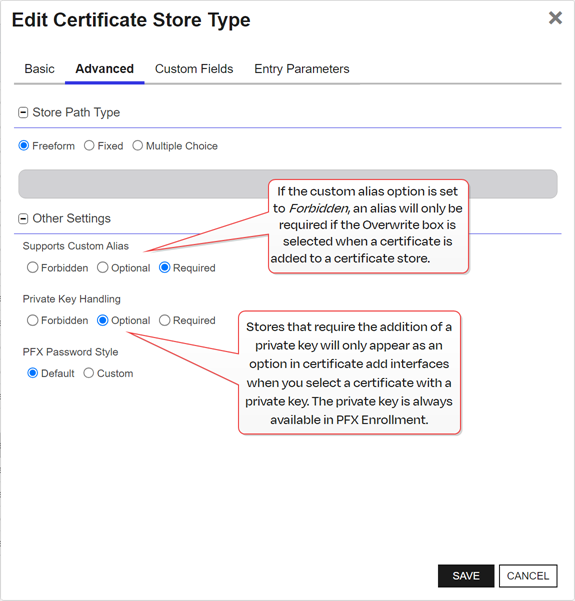
Figure 60: Certificate Store Type Configuration: Advanced Tab
-
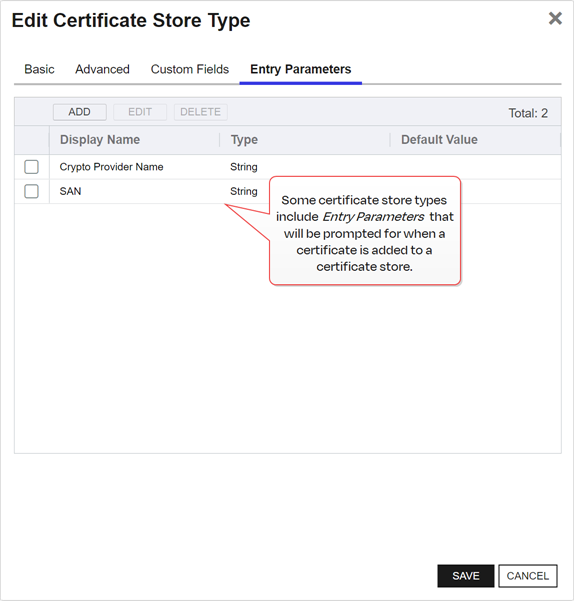
Entry Parameters
Not all certificate store types will have entry parameters. The ones shown in Figure 61: Certificate Store Type Configuration: Entry Parameters Tab are for the custom Windows Certificate type for the Keyfactor custom-built IIS Certificate Store Manager extension (see ).
-
- Click Save to import the certificate to Keyfactor Command
You can also find the help icon (![]() ) at the top of the page next to the Log Out button. From here you can choose to open either the Keyfactor Software & Documentation Portal at the home page or the Keyfactor API Endpoint Utility.
) at the top of the page next to the Log Out button. From here you can choose to open either the Keyfactor Software & Documentation Portal at the home page or the Keyfactor API Endpoint Utility.
Keyfactor provides two sets of documentation: the On-Premises Documentation Suite and the Managed Services Documentation Suite. Which documentation set is accessed is determined by the Application Settings: On-Prem Documentation setting (see Application Settings: Console Tab).